Dunning Best Practices: Minimizing Passive Churn
Losing valued customers due to payment failures, also known as passive churn, can be frustrating. To tackle this, dunning strategies are essential.
Recovering failed subscription payments can be done in two main ways:
1. Retry the existing credit card.
2. Request a new credit card from the customer.
Even small errors in recurring payments can significantly affect growth due to the compounding effect of lost revenue.
Who are we? Churn Buster has been helping subscription companies fix their billing problems since 2013, working with some of the fastest-growing E-commerce and SaaS companies in the world.
While safeguarding billions of dollars of subscription revenue, we've learned exactly what works and what doesn't.
In this guide we’ll show you how to reduce involuntary churn like a real pro.
1. Skip Pre-dunning.
Pre-dunning used to be a dunning best practice.
Years ago, companies sent warning emails to customers 30, 15, and 3 days before their card expired. These pre-expiration emails were called “pre-dunning.”
Today, Stripe, Braintree, and other payments platforms will automatically update cards that have an upcoming expiration date. They communicate directly with the card issuing bank, and the results are impressive.
Over 70% of upcoming expiration dates get updated behind-the-scenes.
Consequently, pre-dunning often results in unnecessary customer tasks due to false alarms. Instead, focus on value-adding communication and let card updates run their course.
2. Optimize Email Timing ✉️
Basic dunning setups will send emails each and every time a payment fails.
This is the entry point for most businesses, and provides little control over optimizing the recovery process.
However, it benefits companies of all size to decouple emails from payment attempts. It's possible to build this in-house, or more advanced tools like Churn Buster can do this for you.
An average of 21% of payments are resolved within the first few days—simply by retrying the card-on-file *before* sending emails.

Right out of the gates, that means 21% fewer emails being sent every month. This often adds up to thousands of customers who are happily unaware there was a (temporary) billing issue.
Side benefit: By allowing time to resolve payments via reattempts, your recovery metrics will actually make sense. When emailing right away for a card update, there is no way to separate necessary card updates from frivolous ones.
The success of the subscription model relies on continuity.
Doing nothing when payments fail isn’t an option, but waiting for the right time to intervene… that’s a best practice. This is why we've made passive recovery via card retries priority #1 at Churn Buster, treating card updates as a last resort.
Churn Buster offers frictionless churn recovery with custom dunning emails, support escalations, SMS messaging, and more.
3. Simplify Card Updates📱
When someone signs up for a subscription service, the expectation is automatic payments that they don’t have to concern themselves with.
In order to gain positive responses from your update requests, you want to make the experience of updating card information seamless and easy for the customer.
- Make the page mobile-responsive: Most of your customers will update their cards using a mobile device. In fact, we see over 70% of updates happening on mobile devices. They will read your dunning email, click through to the page, and (if you’ve got it set up well), quickly input their information. Done deal. If your card updating page is not mobile-friendly, you risk losing these people to simple frustration– and that’s just not worth it.

- Bypass the log-in: Again, simplicity and ease of use are key on your card update pages. The less friction you add into the process, the more likely your customer is to input that information. If your customer clicks through to update their card info and then is prompted to input a password, you’ve established a real hurdle for them. Most people won’t know the password off the top of their head. Some will guess, get it wrong, and feel frustrated. Neither is a good experience, and neither results in a recovered customer. Simply put, if you ask for a password, and they don’t think you’re worth the time to find it, they will churn.
- Check-in on your pages: It’s easy to forget about card update pages as your company grows. But as site changes are made, things can break. You never want to send a faulty card update page to a customer; it’s a massive load of friction on their experience. Create a schedule to check the functionality of those pages and avoid a massive headache.
4. Personalize Your Emails
In dunning, establishing trust is crucial due to the rise in phishing and scams, making customers cautious about links requesting credit card details.
The solution? Personalization. Beyond just using the customer’s first name or engaging copy, subtle changes can significantly enhance trust.
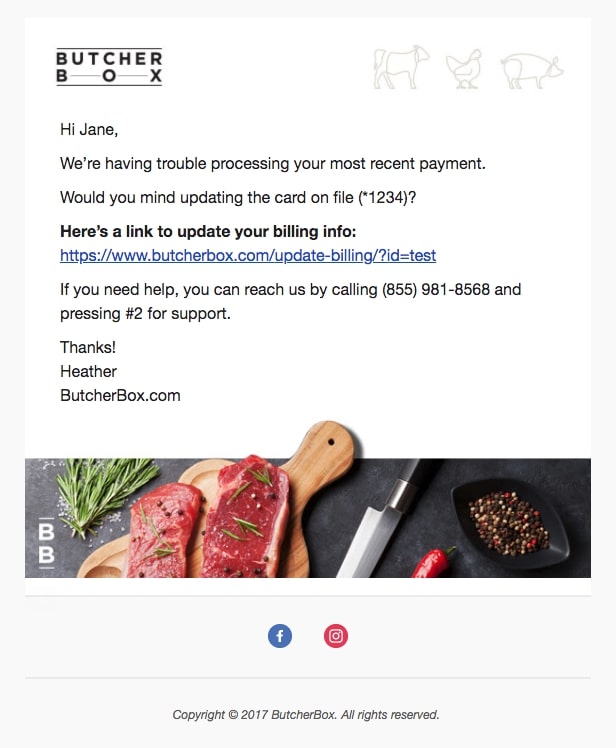
These are transactional emails to existing customers, so trust in the sender is paramount, even more than the email content itself.
Quick tips for boosting personalization and trust:
- Maintain consistent branding: Align the look of your transactional emails with your marketing ones. Consistent branding, like including the most current version of your logo, reassures customers. It's also a best practice to include at least one plain-text email in your dunning sequence, as a workaround for customers who block HTML emails.
- Use a recognizable “from” name: Ensure the sender name is familiar and clearly associated with your organization to avoid customer anxiety. Decide on the sender identity based on what your customers are accustomed to, whether it's a personal touch or a generic company email. Adjusting the sender based on the urgency level of the email can also be effective.
- Refine the email copy: Tailor each email in your dunning series to reflect increasing urgency as the account approaches cancellation. The tone and style should match your brand to maintain trust. Vary the content while keeping it aligned with your brand voice.
- Limit links and CTAs: To direct focus towards updating payment information, restrict your email to a single call to action and minimize links or promotions.
- Set up a reply system: Ensure replies to your dunning emails are directed to someone who can address them promptly, maintaining customer engagement and trust. Even if emails appear to come from high-level executives, the reply-to should be manageable and responsive.
5. Boost Email Deliverability
While ensuring deliverability is a no-brainer for marketing emails, many companies fail to consider this key aspect when it comes to transactional emails–and it’s costing them.
Transactional emails often carry a much heavier weight than your marketing emails. Everything from password resets to, yup, you guessed it, dunning emails, are extremely important to your bottom line. What good is your card update request if it never even reaches your customer’s inbox?
When it comes to dunning, ensuring email visibility should be top priority. Here's how to do it:
- Use a dedicated transactional email service to avoid the deliverability issues common with mixing marketing and transactional emails.
- Implement DKIM/Return-path records with DMARC alignment to build trust with email servers, improving deliverability and your chances of getting paid.
- Monitor for bounced emails to address and rectify deliverability issues promptly. For Churn Buster users, this monitoring can be automated via Slack, webhook, or direct to your email inbox.
- Automate email verification at signup, employing tools like Mailcheck to catch common typos (e.g., name@gmil.com) and reduce incorrect emails in your list.
Focus on practical steps to ensure transactional emails reach customers, thus safeguarding your revenue and background communications.
6. Personal Outreach
While automation is highly efficient for dunning, it's crucial to have safeguards to ensure everything runs smoothly. This includes identifying when a personal touch is necessary.
Develop a method to monitor customers who haven't responded, haven't opened emails, or are high-value clients at risk of leaving. As your automated dunning efforts progress, and if efforts like sending multiple emails yield no engagement, it's a signal to investigate. For example, if a customer hasn't opened any of the five emails sent, their contact details may have changed. Although tracking down the correct information might require extra effort, retaining a high-value customer justifies this.
Is a high-value customer at risk of churning, but have failed to respond to your card update requests? Consider stepping in and sending a personal email (preferably from someone recognizable in your company) and try to get on their radar.
Note: Make sure you get notified of high-value failures. If every failure looks the same to your automated system, a $10 account and a $10,000 account will be treated the same. Set up systems to notify you of high-value failures so you know when to bring in resources and customer success team members to make the save.
Automation is wonderful, and increases business efficiency. But when it comes to dunning, it's also important to know when to manually intervene.
7. Focus on Key Metrics 📊
Performance visibility is often missing from in-house dunning setups.
And for setups with dashboards provided, poorly attributed metrics can create a misleading picture of where value is being created.
For services that charge based on performance, understanding how performance is attributed is crucial. Without clarity, optimizing your strategy as your business scales becomes challenging.
Churn Buster offers detailed insights into every customer and their campaign history, so you can recover as much recurring revenue as possible, even when manual intervention is required.


Besides tracking performance statistics, it's vital to keep tabs on your customers who encounter payment issues.
Here are some good things to know:
- Current past-due customers (those who have missed payments and are unresolved or not yet marked as churned).
- Each customer's stage in your recovery "funnel" (e.g., received 3 of 5 planned emails, next email scheduled for Friday).
- The reasons behind successful payment recoveries, such as whether a customer updated their payment method and the timing related to your outreach efforts.
- Email deliverability (are they making it to customer inboxes?).
- Are your card update pages loading reliably?
While these metrics might not always lead to immediate action, they will, over time, deepen your understanding of your business, which is invaluable. For instance, noticing a decline in payment reattempt success could prompt investigations into the cause, like an increase in customers using prepaid cards or banks marking your charges as suspicious.
Low email open rates could signal issues with email authentication (related to DKIM records and DMARC alignment), overly aggressive or passive subject lines, or emails being marked as spam.
Gaining a comprehensive understanding of these aspects not only helps you pinpoint and address potential issues but also assures you that your systems are functioning correctly. This is especially comforting when dealing with thousands of billing-related communications, ensuring you can rely on more than just hope that your processes are effective.
8. Keep Your Setup Well-Maintained 🔧
Maintaining your system isn't just a one-off task. It's crucial for ensuring smooth operation and avoiding costly oversights that can take months to identify.
After setting up your system, it's essential to continuously check for issues like broken links, unresponsive pages, email deliverability problems, and updates to your payment processor's API. Remember, if you can measure it, you can improve it. Identifying and addressing failures promptly is key. Automation and tools like Slack alerts can streamline monitoring, but ensure someone is responsible for responding to these alerts.
Consider scenarios like a customer updating their card, but the payment fails and they don’t retry. You might inadvertently restart the dunning process or stop outreach altogether. Being proactive in such cases can make a difference.
Adjust your system as needed to provide the right customer experience automatically.
9. Implement Emergency Protocols
Certain issues, like UX problems or critical system failures, require immediate attention. Establish alert systems for your payment processing and dunning operations to catch critical issues as they occur.
For example, if a code update causes your card update pages to go down, can you identify affected customers? Are emails still being sent during an email service provider's downtime?
Without prompt emergency responses, these issues can lead to missed renewal opportunities.
10. The Power of Following Up
Persistence is key in both sales and retention efforts. Despite fears of over-communicating, the actual spam rate for dunning emails is typically below 0.05%.
Customer responses and card updates can occur at any stage, highlighting the importance of not giving up too soon. People get busy, distracted, or might be waiting for a new card. Sometimes, all they need is a reminder.
Wrapping Up:
Failed payments can be a silent killer for your company, if you don’t handle them properly.
With the right dunning management, this avoidable issue can be effectively addressed, preserving your revenue. Churn Buster offers comprehensive tools and strategies tailored to your unique business needs, helping you combat involuntary churn and keep your customer base strong.
When you’re hustling to grow your customer base, it’s frustrating to churn customers.
Churn Buster is your ally in fighting churn, equipped with expert knowledge and solutions tailored for subscription eCommerce and SaaS. Take action against churn by exploring what Churn Buster can do for you.

